from North Shore
Read the full text, including visuals, online as a PDF.
Find the full text ready for printing as an imposed PDF.
Since the commencement of Operation Al-Aqsa Flood, millions around the world have taken to the streets in support of Palestine against the genocidal Zionist entity. We are, globally, in an unprecedented moment of anti-imperialist mobilisation, which threatens not only the Zionist occupation but the colonial powers that uphold it.
This text was written through the summer and early autumn of 2024 from Anishinaabe and Haudenosaunee territory (so-called Southern Ontario, Canada), where people, many new to the left, have been facing intensified violence and harassment from both police and Zionists. Protests are regularly met with arrests and other attacks, which have created a climate of fear among attendees and organisers.
At the same time, that fear, combined with a disconnect from previous generations of struggle and an often-unchallenged fear of militancy, has led to practices that end up putting our comrades in more danger. This text hopes to address one such recurring issue.
what is bad-jacketing?
“Bad-jacketing” (or “cop-jacketing,” “fed-jacketing,” or “snitch-jacketing”) is the practice of accusing people of being a cop, informant, fascist, or other kind of bad actor on specious or non-existent evidence.
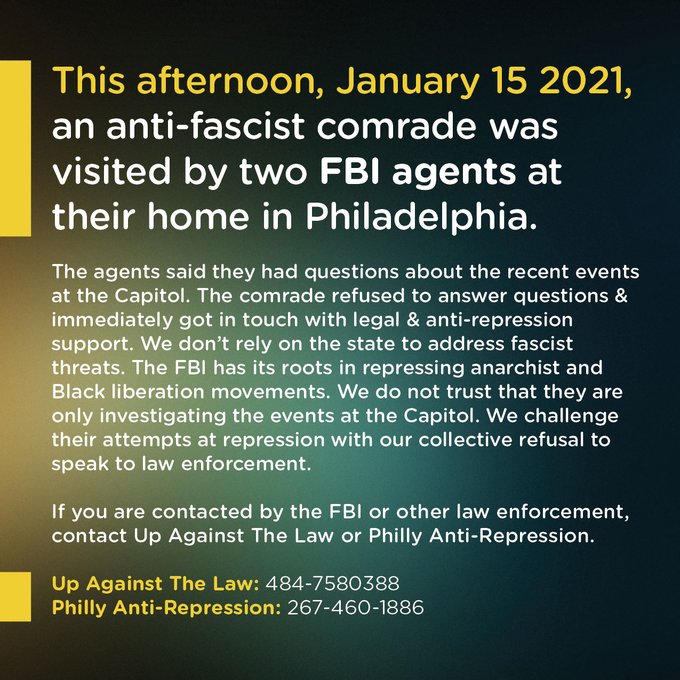
The term has been used since at least the 1960s, where it primarily described COINTELPRO operations that bad-jacketed legitimate members of the Black Panther Party and other organisations. It was, ironically, rumours from infiltrators consolidating their own positions that led to organisations not only isolating but, in some cases, severely beating or executing innocent individuals.
why is bad-jacketing a problem?
A 2015 text titled “No badjacketing: the state wants to kill us; let’s not cooperate” by the Twin Cities GDC, Local 14, says:
- At the least, it pushes away people who have, or are willing, to do work and make sacrifices for the movements.
- Worse, it silences entire groups by sowing mistrust within them and making discussion of strategy and tactics difficult.
- Very commonly, those accused of acting as informants become so alienated from their accusers that they actually become snitches.
- Worst-case scenario, people die. That worst-case scenario is all too common and real, and there is a famous regional history to it as well, in the case of Anna Mae Aquash, a Native American woman from Canada who had worked and sacrificed tireless for the American Indian Movement, or AIM.
Southern Ontario in 2024 is, of course, not the US in the 1960s and 1970s. Our contemporary movements do not act on false accusations of snitching by killing the accused. And while we know that the police are trying to infiltrate us and turn people into informants, the vast majority of these accusations are definitely not coming from people on the state’s payroll.
The biggest threat that bad-jacketing poses to us, here and now, is that it singles people out for state repression. Militants are more likely to be on the receiving end of these accusations, but also, anecdotally, people of colour, neurodivergent people, and anyone who “does not belong” (and, of course, people who fall into all of those categories). In doing so, the people who make these accusations in effect carry out the work of the state. They reproduce the oppressive dynamics of the outside world and push people out – often, the very people our movements are supposed to be fighting for. By pushing them out, bad-jacketing then denies support to people who are often already at heightened risk of criminalisation. It makes people into easy targets, signaling to the police that they can get away with brutalising, arresting, and jailing someone without outcry from the community.
During the 2020 Black liberation uprisings in the US, posts flooded our feeds, warning of “agents provocateur.” Decontextualised videos of police unloading bricks spread like wildfire among both far-right and far-left social media networks. Fascist fear-mongering about out-of-town “ANTIFA” inciting riots trickled down into leftist hyper-vigilance against “white outside agitators.” These warnings often ventured into the realm of conspiracy theories, where protests with unknown organisers or cop cars on fire were signs of a police set-up.
All this has had devastating consequences. The normalisation of this paranoid urge to see false flags around every corner has empowered people “on the left” to share images and openly work to identify individuals carrying out illegal actions. Contrary to what they may believe, these people’s efforts to “root out infiltrators” have in many cases now become the actual basis for the state to arrest and jail its opponents.
Beyond that, bad-jacketing leads to feelings of insecurity and distrust that can tear apart a movement – even without any real infiltrators being involved. Both online and on the ground, we can hear breathless accusations that someone at a protest is an undercover Zionist operative, often for no reason beyond that “they make us look bad.” Zionists, constantly on the lookout for ammunition against us, gladly stoke the flames. Projects like the “Shirion Collective,” a Zionist doxing campaign that claimed on social media to be training undercover operatives, see and celebrate when the left eats its own. We must be equally vigilant against these psychological attacks, which are more subtle and yet can do more damage than any one undercover’s testimony.
“professionally trained to make us look bad”
– Kristina Beverlin on Isaiah Willoughby
On October 5, 2021, Isaiah Willoughby, a Black man, was sentenced to two years in prison for lighting a fire outside an abandoned police precinct in Seattle in June 2020. Willoughby acted because of the murders of Manuel Ellis, his former roommate, and George Floyd at the hands of the police.
When it happened, Kristina Beverlin, a white woman who now wears a kufiya and a “Free Palestine” hat in her profile picture, immediately blasted out a photo of Willoughby. She tweeted that he “just tried to start a fire at the abandoned precinct” and called on “everyone in Seattle to retweet the photo of this man.”
In subsequent tweets, she stated her belief that “SPD wanted the precinct to catch fire to make the peaceful protesters look bad, after SPD had looked like monsters for days.”
It was her initial tweet that appeared in a court affidavit against Willoughby, and her photo that the police disseminated to identify him. In other words, it was this white woman’s insistence that the police wanted someone to set fire to the precinct, and that anyone who did so could only have been directed by the police, that sent a Black man to prison. Like any other white vigilante, the self-deputised liberal peace police will discipline, with violence if necessary, Black or people of colour who step out of line. Unlike any other, she does it in the name of anti-racism, with an #ACAB hashtag in the same breath.
Similarly, social media users widely disseminated photos of a white woman suspected to have carried out the arson of the Atlanta Wendy’s where police murdered Rayshard Brooks. That she was white was proof to them that bad actors with no connection to the movement were behind property destruction during the uprisings, and that without those bad actors, the protests would have been peaceful. As it turned out, the woman in question was Natalie White, who Brooks had called his girlfriend on the night of his death. Two Black men, Chisom Kingston and John Wesley Wade, were later charged for the Wendy’s arson as well. As of December 2023, White and Kingston had accepted plea deals for probation, a fine, and community service, while Wade was scheduled to go to trial.
In both these examples, the people who sought to identify state agents “instigating” at protests were ultimately the people who acted as cops. The gravity of these actions cannot be overstated – they, and we, already know that police kill and torture Black people on the streets, and prison guards do the same against their captives on the inside.
Following the May 2022 leak of the US Supreme Court’s decision to overturn Roe v. Wade, Jane’s Revenge shared a communiqué about the fire-bombing of a predatory anti-choice “pregnancy centre” in Madison. The action sparked the usual uproar among the right about “woke ANTIFA terrorists” waging war against Christianity. But rather than defend the action’s righteousness, much of the left instead occupied itself with speculation about whether cursive graffiti and a “too-neat” circle-A meant that it was a false flag. The underlying logic here was that if something looked “too perfect,” if it made the right too angry, it couldn’t possibly be real. We may talk of rioting against the Supreme Court, but no one seriously means it.
In response to the right-wing outrage campaign about Jane’s Revenge, the FBI offered a bounty of up to $25,000 for information. Days later, in January 2023, the US Department of Justice indicted two people for graffiti on anti-abortion centres in Florida, actions that were also broadcast through Jane’s Revenge. The Florida investigation eventually produced in a total of four arrests, all but one of the defendants being women of colour. Worse, the Florida 4 were prosecuted under the FACE Act, a law intended to protect abortion access. Meanwhile, an investigation that involved 11 different state agencies and the FBI’s Joint Terrorism Task Force culminated in the March 2023 arrest of Hridindu Sankar Roychowdhury for the Madison fire-bombing. Though the right jumped at the opportunity to gloat, widely publicising the defendants’ photos and personal information, charges against Roychowdhury and the Florida 4 received little attention from the left. Roychowdhury pled guilty after being denied pre-trial release and was sentenced to 90 months (7.5 years) in federal prison on April 10, 2024. Three of the Florida 4, after taking felony pleas that avoided convictions under the FACE Act, were also handed down prison time on September 12 of this year, ranging from 30 days to 1 year and 1 day. Popular support may not have prevented those prosecutions, but the significance of solidarity shouldn’t be understated. Instead, much of the left’s message to militants turns out to have been: “we’ll call you feds, and when it turns out we were wrong, we’ll abandon you anyways.”
Though we never had our own Third Precinct moment, left networks in Ontario fell victim to many of the same conspiratorial impulses. Reposted Instagram stories warned of “suspicious piles of bricks” left as bait near march routes and even “black blocs from Montréal” coming into town to start riots.
While, regrettably, no such riot materialised here in 2020, the bad-jacketing of the black bloc has a long history in Southern Ontario, as in other regions. A particularly egregious example came in the wake of the Toronto G20 in 2010, where liberals convinced themselves that the property damage was all an inside job and set out looking for proof. They singled out a muscular white man in combat boots and “cop-like” black pants for looking suspicious, digging up every image of him they could find. All of this crowd-sourced evidence built a convenient case for the police, who arrested and jailed the target of their suspicions.
A pattern emerges: subsequent repression draws only a fraction of the concern that the broad left had earlier put into interrogating the legitimacy of an action. This is one of the most insidious functions of badjacketing and disavowal – it aids the state project of disappearing people. Speculation about false flags, made exponentially worse by social media and algorithms that egg on endless engagement, steals away energy that could be spent preparing for the repression to come. It turns actions into abstractions ripe for every person to project their own arguments. That abstraction removes militants’ humanity from the picture, enjoining us to forget that real people, putting their lives on the line for the movement, must have lit the match or thrown the brick. The collective failure to adequately show up for each defendant and prisoner in this section – and many more not named – goes beyond a culture of disposability. It is a mass forgetting that makes each of us who partakes in it complicit in the work of the police, prisons, and the carceral state to not only extinguish our resistance but also erase our memory of its very possibility – and our memory and connection to the people who’ve sacrificed to keep that possibility alive.
when people are occupied, resistance is justified
The movement for Palestine has long been one of the most hyper-surveiled and attacked. Only when it comes to the Palestinian struggle will even the most mild, pacifist expressions of support land someone on McCarthyist blacklists like Canary Mission, extensive repositories of personal information stretching back years. It is no wonder, then, that people are – correctly – concerned about being targeted by our enemies, which include not just the settler colonial state itself but also Zionists who self-organise outside of it.
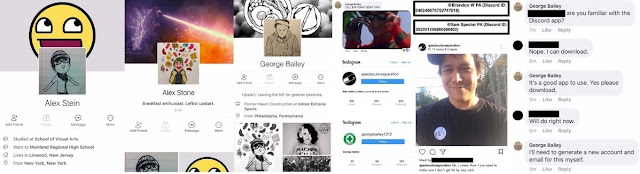
Unfortunately, this has once again meant a dangerous resurgence of bad-jacketing. In February 2024, social media posts from the “Shirion Collective” sparked mass outrage and panic among supporters of Palestine. Announcing an “Operation Global Insight,” the posts claimed to be launching an “undercover operation” in key locations such as Toronto. “Volunteers willing to wear keffiyehs and walk [masked] in these demonstrations” would “be provided an hour long basic training by one of [their] ex-Mossad team leads.” Further, “individuals with Arabic-sounding names and Middle Eastern appearance may be uniquely positioned for deeper infiltration and will receive cash compensation for their vital role in [the] operation.”
Though the collective is, without a question, real, there is plenty of reason to believe that the reaction to the post was disproportionate to their actual abilities. Sensationalist claims of Mossad ties in an emoji-studded public tweet do not paint a picture of a sophisticated intelligence operation. Neither do their existing “exposés” on social media, which, despite techno-babble buzzwords about AI, are largely limited to reposting other people’s footage and open-source information that anyone with access to Google could easily retrieve. The description of walking around at protests and “law enforcement presence” suggests no actual knowledge of how Palestine solidarity groups organise or bring in new members. A few people with bad intentions joining a march of hundreds or thousands, where every angle is already recorded and streamed live on Instagram, can hardly be characterised as “infiltration.”
If that were not enough on its own, the White Rose Society, an anti-fascist research group, shared internal screenshots from Shirion’s Telegram channel that confirmed the post’s real purpose was to sow fear and distrust. One Shirion volunteer is quoted as saying:
We won’t need to do anything. They will:
- Tone down
- Police their own
- Maybe even beat up their own just because they think those are us
That summary of their goals succinctly re-states the risks that bad-jacketing poses to our movements.
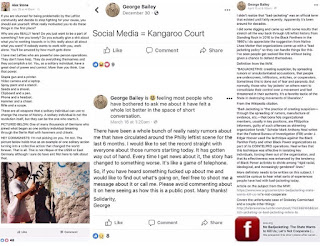
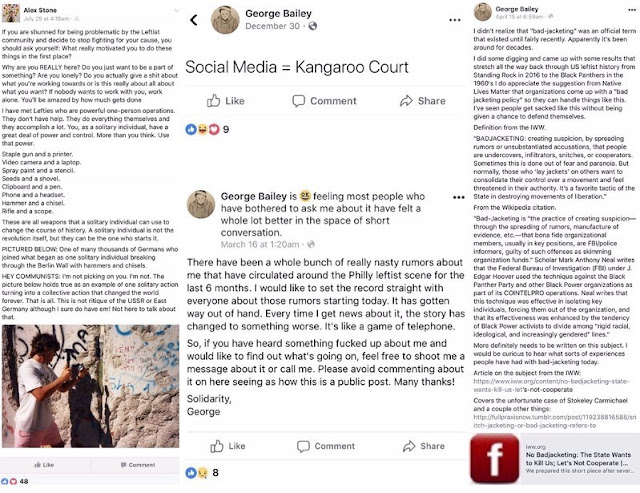
Even before the Shirion scare, claims that someone was secretly a Zionist or cop were already commonplace. People who wear the symbols or fly the flags of the Palestinian resistance have been accused of being “agitators,” sent by Zionist organisations like B’nai Brith to make protestors look bad. Over-the-shoulder glimpses of someone’s phone or poor fashion choices have been presented as evidence that a protestor is actually an undercover. Online, Palestinians have been accused of being Zionist sockpuppets off of little more than bad feelings. And, naturally, even minor disagreements or political critiques will end in allegations that so-and-so is a fed. While, thankfully, conspiratorial crowds here have not at least yet handed over one of our own to the cops, these accusations are sometimes accompanied by calls to act against someone. In one case recently, a queer person of colour known to other attendees was followed, harassed, and filmed aggressively at a protest because someone had decided for no clear reason that they were a Zionist in disguise.
As the police continue to crack down on us, it is all the more crucial that we learn from the mistakes of the recent past. We cannot let our rightful vigilance lead us to attack our own comrades. Nor should we water down our political lines, our demands, or our tactics for fear that the media and the right will smear us – they do that regardless. It may not be possible to eliminate some, faint chance that an infiltrator is behind a resistance flag, a punch thrown at a Zionist, a brick through a window, but far more likely is that some brave person, who has chosen to more boldly and unabashedly confront this genocidal system and its supporters, is responsible. For that, they deserve our support and our solidarity against whatever repression may come, not our condemnation.
knowing our enemies
An over-emphasis on undercovers may lead to an under-emphasis on other security vulnerabilities. Rather than acting according to a one-size-fits-all checklist or, worse, reacting to threats only as they appear, it’s important to proactively identify and individually study threats in order to understand how to address them. That is to say, what – specifically – is your enemy trying to do? How do they do it? The process of answering these questions is known as threat modeling.
Accounts like Shirion, Leviathan, or StopAntisemitism are real threats, as any of their victims know all too well. But OSINT, as well as everyday acquaintances, are much likelier to be the source of their information.
Your personal Instagram or TikTok page might already give away your identity, the protests you attend, your work or school, and the identities of your friends and family members. Your employer might publicly share profiles, including photos, of all of their staff on their website. Tools like PimEyes and FaceCheck.ID allow anyone willing to pay for them to run facial recognition technology and search the Internet for a given face.
If you’re a student, a Zionist classmate could easily recognise you from criticising racism in class and look up your personal information in a school database. A right-wing former colleague could remember you for being politically outspoken at your shared workplace. Knowing the true identities of everyone at a march will do nothing to prevent doxing if, for example, that march is being streamed online, your face is exposed, and your social media is public.
what about the real infiltrators and provocateurs?
Infiltration – actual infiltration, where someone comes into our organisations and our lives, pretending to be our friend, only to hand information over to the state – should not be taken lightly. But our baseline understanding of it often takes the form of a few convenient tropes, reinforcing existing biases against militancy and justifying dismissiveness towards criticism. These tropes prevent us from truly knowing our enemies.
The late Matt Cicero wrote that:
[there is a] misconception that all infiltrators act as agents provocateurs who try to manipulate activists into taking illegal, violent, unpopular, and ineffective actions. But as Gary T. Marx points out in his theory of social movement infiltration, social movements are damaged by “opposing organizational, tactical, and resource mobilization tasks.” In other words, infiltrators suppress social movements by fomenting divisions and internal conflicts, diverting energies toward defending the movement rather than pursuing broader social goals, sowing misinformation or damaging reputations, obstructing the supply of resources (money, transport, meeting spaces), or sabotaging planned actions. Many infiltrators are thus better described as agents suppressants, who are there to gather intelligence and channel groups away from militant action.
[…]Incidents of provocation can be high-profile and sensational, such as undercover police posing as members of the black bloc at Montebello. This can lead activists to paint all militant action as the work of agents provocateurs, even if there is no evidence that this is true. Conversely, because of the low-profile of most agents suppressants, activists are often unaware of their role and impact in pacifying and controlling social movements.
The spectre of the provocateur itself, then, carries out the suppressant role of “put[ting] a damper on evolving movement militancy.”
The single-minded focus on the agent provocateur often goes hand-in-hand with a short-term view of state repression as having only two main goals:
- Criminalising individuals in order to take them off the board while making an example out of them; and
- Smearing the movement in the media, stigmatising it to the public, by associating it with criminality.
But as Cicero describes, the state is additionally engaged in a long-term project of suppression and counter-insurgency. The police cannot arrest every dissident – but they don’t need to jail us all to successfully maintain the colonial order. The central goal of counter-insurgency is to preserve legitimacy and control.
To that end, some further goals of state repression include, but are not limited to:
- Exploiting existing tensions in the movement in order to sow discord and distrust;
- Defanging the movement by discouraging forms of action that exceed accepted norms of protest; and
- Collecting intelligence to inform repressive operations, for the purposes of criminalisation and suppression.
We should examine the issue of infiltration with all of these goals in mind. David Gilbert says, “[t]here is no simple litmus test to differentiate sincere militancy from provocation or honest caution from suppression.” The same extends to the search for infiltrators more broadly. Most of the time, the only truly conclusive proof that someone is a police infiltrator comes from seeing the evidence against you that they’ve handed over to the state after you’ve been charged. That isn’t of much help – by the time you have those court documents in your possession, the damage will already have been done. That is assuming that the information they collect ever goes to court at all. RCMP documents from the G20 suggest that there may have been as many as 12 undercover officers. Far fewer than that were ever exposed by name, and the remainders’ identities may never be known.
People who’ve experienced the profound betrayal of finding out that someone they knew was an undercover or informant often end up drawing conclusions that are diametrically opposed from one another. But a common thread persists through most of their takeaways: there are few ways to prove for certain that someone is a cop, and many ways that the hunt for infiltrators itself instead undermines our work and furthers the state’s goals.
Accordingly, we should turn our energies to proactively building a security culture that protects us from both infiltration and other security threats. Much has been written on this subject already. In short: solid security practices should mean that an undercover cop is prevented from gathering meaningful information even if we do not know who they are, and that security risks are dealt with regardless of whether an individual is specifically acting on behalf of the state. If you do everything right, a plainclothes still won’t know who among the bloc smashed that ATM, even if they saw it happen with their own eyes.
As the ever-green “Why Misogynists Make Great Informants” reminds us, many of the greatest threats to our movements may not officially collaborate with the police either. In the Toronto anti-fascist scene alone, multiple people accused of misogyny and sexual violence/gender-based violence later went on to renounce the left, consort with their former opponents, and attack (verbally, physically, and with legal threats) their former comrades. None of those people, to our knowledge, were undercover cops, nor were they secretly fascists all along. Looking for a non-existent smoking gun to show that someone was lying about their identity would – and did – only delay people from taking necessary action against them when the myriad of other red flags should have been more than enough.
naming our enemies
The epidemic of bad-jacketing is inseparable from the problem of peace policing. Many organisers advocate for a policy of de-escalation at all costs, even in the face of potentially deadly violence from police and Zionists. They speak of “agitators” who disrupt and “escalate” “peaceful protests” – a nebulous euphemism that they apply to both the Zionist who shows up with a knife and the militant who comes prepared to fight back.
We should be clear: our enemies are not “agitators.”
Our enemies are the police, who brutalise us and lock us away to enforce settler colonial order. Our enemies are Zionists and other white supremacists, who assault and harass us in the streets, and stalk and threaten us in our everyday lives. Our enemies are politicians and other establishment liberals, who carry out colonial and imperialist genocides, here, in Palestine, and around the world, all the while crying crocodile tears about a so-called humanitarian crisis that they created. Our enemies are legacy media institutions, who smear resistance as terrorism and mobilise support for each of these attacks.
We must take care to differentiate between antagonistic and non-antagonistic contradictions, and to distinguish between enemies and potential friends. Too often, we see organisers reject co-strugglers in order to appeal to liberal institutions that will never be on our side. They may frame the conservative path as the only strategic option, rejecting open support for armed struggle, militant direct action, and anything else that would create “bad optics.” Disagreements from co-strugglers are treated as threats worse than that of liberal media, who we must appeal to for sympathy, or Zionists and cops, who we must appease for our safety.
When our enemies attack us anyways, these organisers pin the blame not on the perpetrators but on the co-strugglers who deviate from their line. They forget that to be attacked by the enemy is not a bad thing but a good thing. Our enemies do not strive for unity with us, knowing that ours is an antagonistic contradiction, knowing that our collective liberation requires their annihilation. It is better that we, too, abandon any notions of conciliation and recognise our enemies as enemies.
For all these reasons, we urge people to draw a clear line of demarcation between the enemy and ourselves. Abandon the euphemisms and name our enemies. When we struggle through our differences, let us do so with a shared understanding of what we are for and what we are against.
by every means necessary
Not only is bad-jacketing dangerous, it is disempowering and demobilising. It forecloses entire realms of possibility, insisting that we limit ourselves to the same set of legal, non-violent tactics. It threatens state violence against people who do not comply with those limitations being imposed upon their actions. Many people cannot take the risk of arrest. But something being risky does not make it impossible. Just because some of us cannot act does not mean that no one should.
While its meaning is sometimes lost, respecting a “diversity of tactics” means refusing to impose non-violence upon our co-strugglers and declining to condemn those that destroy property or take up arms. As a group of autonomous UCLA students writes in the wake of vicious assaults on their encampment:
We have noticed a trend of the desire to appear peaceful for the media taking precedent over the right of protestors to self defense, mirroring the world’s response to Palestinians’ right to self defense in the face of blatant fascist attacks and eliminationist violence.
We cannot allow our resistance movement to demand obedience over safety in the same way as western imperialist forces against the colonized.
Without drawing false equivalence with a people living under active bombardment and military invasion, the liberal urge that leads people to denounce burning precincts or fake clinics as “giving police an excuse to crack down” is the same that denounces the Palestinian resistance for “giving Israel an excuse to destroy Gaza.” We must refuse any invitation to distance ourselves as the “good,” “peaceful,” “innocent” ones. Instead, we affirm the right of Palestinians and all people to resist colonial domination by any means necessary.
We would remind our co-strugglers, too, that our enemies do not care about the truth, and they have no conscience. We see this in the viciousness with which the police enforce an unprecedented ban on overpass protests in Toronto, where people rallied on the sidewalk to wave flags and chant. We see it in the eagerness with which a long list of electeds, including the Prime Minister himself, leapt to denounce a protest of a Jewish hospital that never happened. We see it in the adamance with which Zionists call the very existence of Palestinians a terrorist threat against them, no matter how young, no matter how innocent, no matter how non-violent. Right-wing propagandists will fabricate scandals out of thin air, and the establishment will happily take up their version of the story. Even if each and every one of us swears to turn the other cheek to our assailants, as long as we challenge the colonial status quo, in our enemies’ eyes, we will never be peaceful.
Another path is possible, and the movement to Stop Cop City sets a powerful example. In February, a journalist asked spokesperson Mary Hooks of Vote to Stop Cop City whether organisers condemned arsons of police vehicles. She answered:
Hell no. No. Not at all, And to be honest with you, Atlanta deserves more than that. Real talk, they’re lucky, this city is lucky, this country is lucky. Atlanta has its hands in literally murdering Palestinians right now. You think we give a damn about some equipment? Not at all. Not at all.
But some of us, we cannot take that risk. And those who can, bless them. Bless them. I cannot take that risk. But Lord knows, I’ll sit with my lighter and be like, damn.
[…]We need every, every means necessary to deal in the police state we are dealing with. So I don’t care, no, and I would imagine my comrades would say the same. No, not gonna condemn nobody for doing righteously what they need to do when our city has silenced every quote-unquote proper, democratic process.
The movement’s aboveground and clandestine elements are two parts of a whole. Both are necessary for our victory.
Listen to Isaiah Willoughby speak in his own words on Kite Line Radio:
kitelineradio.org/tag/isaiah-willoughby/
Support defendants and prisoners from the George Floyd Uprisings:
uprisingsupport.org
Contribute to the Florida 4’s commissary and find other ways to support through the Anti-Repression Committee of South Florida:
linktr.ee/sfl_arc
more on peace policing
“ACAB Includes Peace Police: Three Report Backs from Palestinian Solidarity Actions” (November 2023) on Archive.org, online at archive.org/details/acab-includes-peace-police-en-print-8/page/2/mode/2up
“Peace Police are Police: How Protest Marshals Sabotage Liberation and Protect the State” (December 2023) on North Shore Counter-Info, online at north-shore.info/2024/03/11/peace-police-are-police-new-zine-classic-image/
more on security
“Confidence. Courage. Connect. Trust. A proposal for security culture” (November 5, 2019) on North Shore Counter-Info, online at north-shore.info/2019/11/05/confidence-courage-connection-trust-a-proposal-for-security-culture/
“Doxcare: Prevention and Aftercare for Those Targeted by Doxxing and Political Harassment” (August 26, 2020) on CrimethInc., online at crimethinc.com/2020/08/26/doxcare-prevention-and-aftercare-for-those-targeted-by-doxxing-and-political-harassment
The Threat Library by the No Trace Project, online at notrace.how/threat-library/
“Threat Modeling Fundamentals” by Håkan Geijer on Riot Medicine, online at opsec.riotmedicine.net
more on infiltration
Fuck the (Hamilton) Police, online at fuckhps.noblogs.org
“Infiltrated! How to prevent political police from undermining grassroots solidarity” (May 1, 2017) in Briarpatch Magazine, online at briarpatchmagazine.com/articles/view/infiltrated
“Living among us: Activists speak out on police infiltration” (July 1, 2011) by Tim Groves, online at briarpatchmagazine.com/articles/view/living-among-us
“Stop Hunting Sheep: A Guide to Creating Safer Networks” (2011) on Sprout Distro, online at sproutdistro.com/catalog/zines/security/stop-hunting-sheep/
“The G20 Main Conspiracy Group: The Charges and How They Came to Be” (2012) on the No Trace Project, online at notrace.how/resources/#toronto-g20-main-conspiracy-group
“Why Misogynists Make Great Informants” (Spring/Summer 2010) by Courtney Desiree Morris on Incite! National, online at incite-national.org/2010/07/15/why-misogynists-make-great-informants-how-gender-violence-on-the-left-enables-state-violence-in-radical-movements/